Log in
Build Your Site
Network Security Key Explained: Everything You Need to Know
Unlock your Wi-Fi's full potential. Learn what a network security key is, how to find it, and how to use protocols like WPA3 to maximize your network's security.

In today's digitally interconnected world, a stable and secure internet connection is no longer a luxury—it's a necessity. We rely on our home and office networks for everything from communication and entertainment to work and managing our personal information. At the heart of this digital fortress lies a critical component: the network security key. You might know it by a more common name, the Wi-Fi password. Understanding what this key is, how it functions, and how to manage it effectively is the first and most crucial step in protecting your digital life. This guide will walk you through everything you need to know about your network security key, ensuring your online activities remain private and secure. Without a robust wireless security key, your personal data, Browse history, and even your smart home devices could be exposed to unauthorized users.
What Is a Network Security Key?
At its most fundamental level, a network security key is a password or passphrase that you enter to connect a device to a secured wireless network. Think of it as the digital key to your online home. When you set up a Wi-Fi network, you create this key to prevent just anyone from connecting to it. Its primary purpose is twofold: authentication and encryption. First, it authenticates your device, confirming that it has permission to join the network. Second, it encrypts the data that travels between your device and the router, scrambling it so that even if someone were to intercept it, they couldn't read it. This process is a fundamental aspect of network access control, a security technique that regulates who or what can view or use resources in a computing environment. While most of us are familiar with a simple string of characters as our Wi-Fi password, in more complex enterprise environments, a network security key can take other forms. It might be a sophisticated digital certificate stored on a device or even biometric information, such as a fingerprint. Regardless of its form, the goal remains the same: to ensure that only authorized individuals can access the network. By locking down access, the wireless security key acts as the first line of defense against a wide array of cyber threats, safeguarding your private information from prying eyes and ensuring the integrity of your network. The importance of a strong network security key cannot be overstated. An unsecured or weakly protected network is an open invitation for malicious actors. They can piggyback on your internet connection, slowing it down for legitimate users. More alarmingly, they can potentially access shared files on your network, inject malware into your devices, or monitor your online activities to steal sensitive information like bank details, passwords, and personal emails. Therefore, understanding and properly utilizing your wireless security keyis not just a technical formality; it's a critical component of your overall digital hygiene and personal security strategy.
How Network Security Keys Work
The functionality of a network security key is rooted in two core principles of cybersecurity: authentication and encryption. When you attempt to connect a new device, like a smartphone or laptop, to a Wi-Fi network, a process often referred to as a "handshake" occurs. Your device sends a request to the router, and the router, in turn, asks for the network security key. You then enter the Wi-Fi password. If the key you provide matches the one stored in the router's configuration, your device is authenticated and granted access to the network. This authentication step ensures that only devices with the correct credentials can join.
Once your device is connected, the second and equally vital function of the wireless security key comes into play: data encryption. As you browse the internet, send emails, or stream videos, data is constantly flowing between your device and the router. The security protocol in use (such as WPA2 or WPA3 encryption) uses the network security key to create an encrypted tunnel for this data. This means that all the information is scrambled into an unreadable code. Even if an unauthorized party manages to intercept this data transmission, they won't be able to decipher its contents without the corresponding key. This in-motion encryption is essential for protecting your activities from eavesdropping and man-in-the-middle attacks, where an attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. By preventing unauthorized access and encrypting your data, the network security key serves as a powerful shield against a variety of digital threats. It effectively blocks casual snoops, neighbors looking for free internet, and more determined hackers from compromising your network's integrity. Without this fundamental layer of security, your online world would be transparent, leaving your personal and financial information vulnerable to theft and exploitation. This is why selecting a strong key and the right security protocol is a cornerstone of learning how to protect Wi-Fi network connections effectively.
Types of Network Security Keys & Protocols
The effectiveness of your network security key is heavily dependent on the underlying security protocol your router uses. Over the years, wireless security protocols have evolved to counter increasingly sophisticated threats. Understanding the differences between them is crucial for ensuring your network is as secure as possible. The main protocols you will encounter are WEP, WPA, WPA2, and the current gold standard, WPA3 encryption.
Let's explore the evolution and security levels of these protocols, highlighting the critical differences in our WEP vs WPA2 and WPA3 comparison.
- Wired Equivalent Privacy (WEP): This was the first security protocol for Wi-Fi and was introduced in 1999. As its name suggests, it was designed to provide a level of security comparable to a wired network. However, WEP is now considered obsolete and highly insecure. It uses the RC4 stream cipher for encryption, but significant vulnerabilities were discovered that allow attackers to crack a WEP key in a matter of minutes using readily available software. If your network is still using WEP, it is imperative that you upgrade your security settings immediately.
- Wi-Fi Protected Access (WPA): WPA was introduced as an interim replacement for WEP to address its glaring flaws. It offered stronger encryption through the Temporal Key Integrity Protocol (TKIP). While a significant improvement over WEP, TKIP was designed to work with older hardware and was eventually found to have its own vulnerabilities. WPA provided a much-needed security boost at the time but is no longer considered secure enough for modern threats.
- Wi-Fi Protected Access II (WPA2): For over a decade, WPA2 has been the standard for securing wireless networks. It replaced TKIP with the much more robust Advanced Encryption Standard (AES), which is still used by governments and security organizations worldwide. WPA2 provides a high level of security and is the minimum standard you should be using for your home network. However, even WPA2 is not infallible. A significant vulnerability known as KRACK (Key Reinstallation Attack) was discovered in 2017, which could, under specific circumstances, allow attackers to read encrypted information.
- Wi-Fi Protected Access 3 (WPA3): Introduced in 2018, WPA3 encryption is the latest and most secure protocol. It addresses the vulnerabilities of WPA2 and introduces several key improvements. It uses a more secure handshake method called Simultaneous Authentication of Equals (SAE), which makes it much harder for attackers to crack passwords by guessing them offline. WPA3 also provides individualized data encryption on open networks (like in cafes or airports), meaning your connection is encrypted even if you don't enter a password. For optimal security, you should use WPA3 encryption if your router and devices support it.
Here is a comparison to help you visualize the differences:
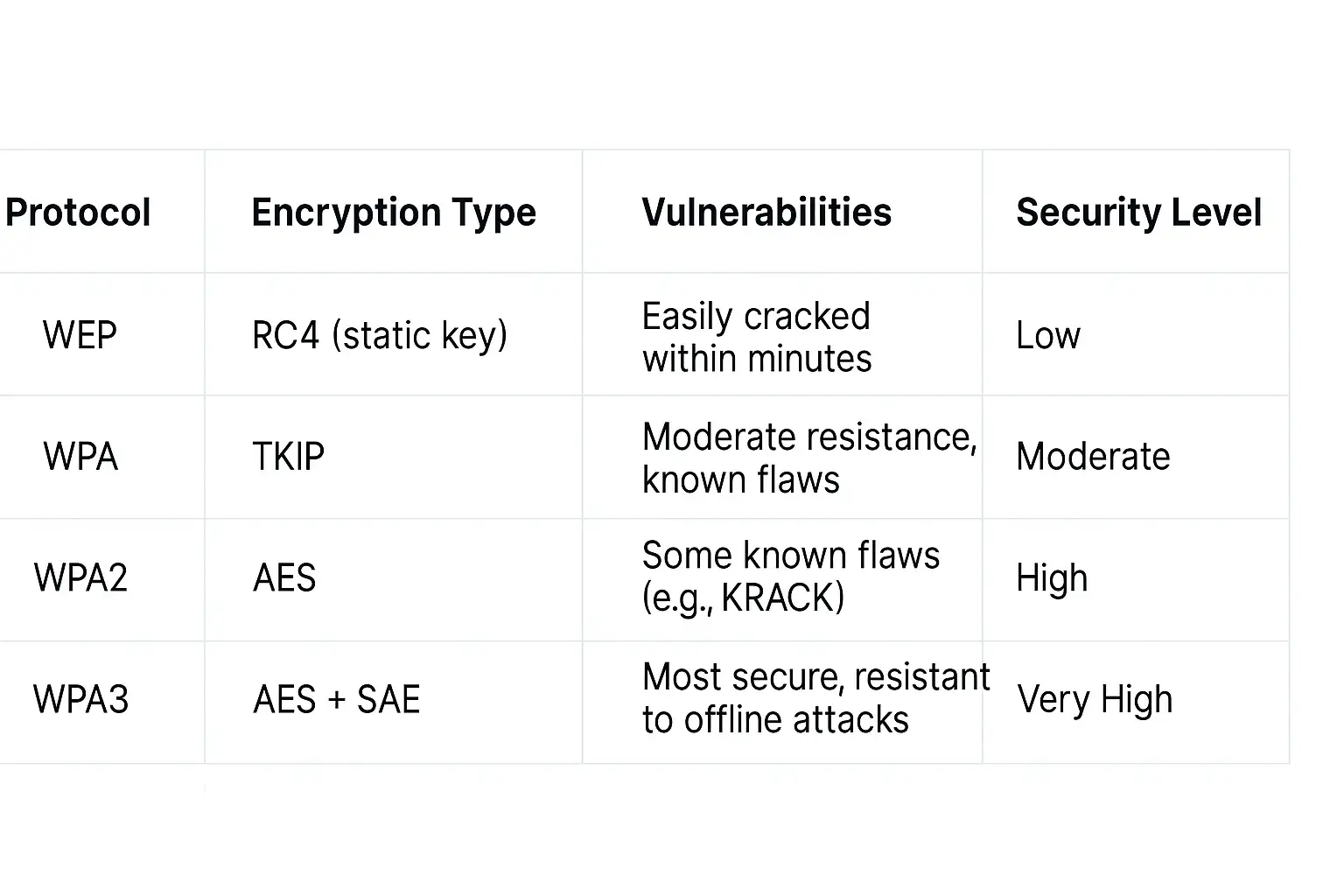
Given the clear advantages, migrating to WPA3 encryption is one of the most effective steps you can take to secure router and network connections. It offers the most advanced protection currently available for your wireless security key.
How to Find Your Network Security Key
Forgetting your Wi-Fi password is a common and often frustrating experience. Fortunately, there are several straightforward methods to find Wi-Fi password information, whether it's printed on your router or stored within your devices' settings. Here’s a platform-by-platform guide to locating your network security key.
- Check the Router Label: The simplest method is often the most overlooked. Most internet service providers (ISPs) and router manufacturers print the default network name (SSID) and the network security key on a sticker located on the back or bottom of the router itself. Look for terms like "Wi-Fi Key," "Password," "Passphrase," or "Wireless Key." While you should ideally change this default password for better security, it's the first place to look if you haven't.
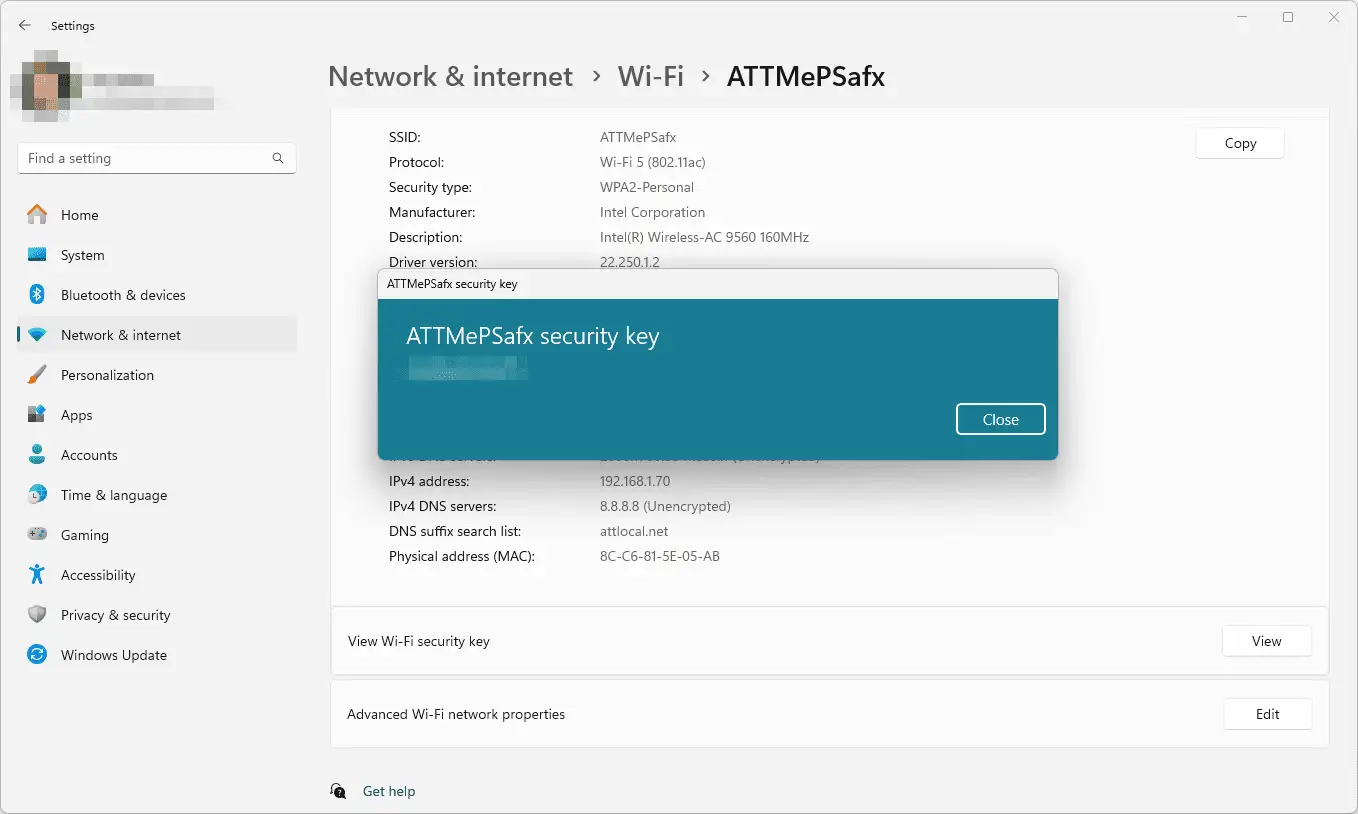
- On a Windows 10/11 Computer: If you have a Windows PC that is already connected to the Wi-Fi network, you can easily find the key.
- Navigate to the Control Panel.
- Go to "Network and Internet" and then "Network and Sharing Center."
- Next to "Connections," click on your Wi-Fi network name.
- In the Wi-Fi Status window that pops up, click on "Wireless Properties."
- Go to the "Security" tab and check the box that says "Show characters." The password will be revealed in the "Network security key" field.
- On a macOS Computer: macOS also stores your Wi-Fi passwords in a secure utility called Keychain Access.
- Open the "Keychain Access" application (you can find it using Spotlight search).
- In the search bar in the top-right corner, type the name of your Wi-Fi network.
- Double-click on the network name in the results.
- In the new window, check the "Show Password" box. You will need to enter your Mac's administrator password to view the wireless security key.
- On newer versions of macOS (like Ventura and later), you can also go to System Settings > Wi-Fi, click the three-dot menu next to your network, and select "Copy Password."
- On an Android Device: Modern Android versions make sharing and viewing Wi-Fi passwords simple.
- Go to Settings > Wi-Fi (or Network & Internet).
- Tap on the gear icon next to your connected network or tap the network name itself.
- You should see a "Share" button. Tapping it will display a QR code that others can scan to connect. Below the QR code, the Wi-Fi password is typically displayed in plain text. You may need to verify your identity with your fingerprint or PIN first.
- On an iOS Device (iPhone/iPad): For a long time, iOS did not allow users to view saved Wi-Fi passwords directly. However, starting with iOS 16, this has changed.
- Go to Settings > Wi-Fi.
- Tap the "i" (information) icon next to the network you are connected to.
- Tap on the "Password" field. You will need to authenticate with Face ID, Touch ID, or your passcode to reveal the network security key.
- Access the Router's Admin Panel: If none of the above methods work, you can always find the key by logging into your router's administrative interface.
- Find your router's IP address (commonly 192.168.1.1 or 192.168.0.1).
- Open a web browser and enter this IP address into the address bar.
- You will be prompted to log in with the router's admin username and password (which might also be on the router's sticker, unless you've changed it).
- Once logged in, navigate to the wireless or Wi-Fi settings section. The network security key will be displayed there. This is also the place where you can change Wi-Fi key settings.
Managing & Securing Your Network Security Key
Simply having a network security key is not enough; managing it properly is essential for robust protection. A weak, default, or compromised key can undermine the security of your entire network. Following best practices for creating and maintaining your Wi-Fi password will significantly enhance your digital safety. Here are actionable tips to secure router connections and protect your key.
- Create a Strong, Unique Password: The strength of your wireless security key is your first line of defense. Avoid common and easily guessable passwords like "12345678" or "password." A strong password should be:
- Long: Aim for at least 12-16 characters. The longer, the better.
- Complex: Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Random: Avoid using personal information like names, birthdays, or addresses. Consider using a passphrase—a sequence of random words—which can be both memorable and highly secure.
- Change Your Wi-Fi Key Regularly: It's good security hygiene to change Wi-Fi key credentials every three to six months. This practice limits the window of opportunity for anyone who may have gained unauthorized access to your network. Regular changes ensure that old, potentially compromised keys are no longer valid.
- Disable Wi-Fi Protected Setup (WPS): WPS is a feature designed to make connecting devices easier, often with the push of a button. However, certain implementations of WPS have known vulnerabilities that can be exploited by attackers to gain access to your network, bypassing your network security keyaltogether. Unless you absolutely need it, it's recommended to disable WPS in your router's settings.
- Set Up a Guest Network: Most modern routers allow you to create a separate guest network with its own name and password. This is an excellent way to provide internet access to visitors without giving them access to your main network and all the devices connected to it, such as your computers and network-attached storage. This segmentation is a key principle of how to protect Wi-Fi network integrity.
- Employ Additional Security Layers: A strong Wi-Fi password is foundational, but it works best as part of a multi-layered security strategy.
- Enable the Firewall: Ensure your router's built-in firewall is turned on.
- Keep Firmware Updated: Regularly check for and install firmware updates for your router. These updates often contain critical security patches.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic, adding another layer of privacy that protects you even if your Wi-Fi network were to be compromised.

By diligently applying these management and security tips, you transform your network security key from a simple password into a robust component of a comprehensive defense system for your digital life.
Hardware Options to Secure Keys
For users and businesses that require an even higher level of security beyond a strong password, several hardware solutions exist to protect credentials and manage network access. These devices are designed to secure cryptographic keys and make authentication processes resistant to online attacks like phishing and malware. While some are more geared toward enterprise environments, others are accessible to security-conscious individuals looking to fortify their digital lives.
- Yubico Security Key: Yubico is a well-known name in hardware-based authentication. Their security keys, like the Yubikey series, support multiple protocols including FIDO2, which is the standard for passwordless authentication. You can use these keys as a form of multi-factor authentication for logging into services, and in some advanced setups, they can be part of the network access control system, requiring the physical key to be present to authorize a new device.
- Nitrokey: Nitrokey offers a range of open-source security hardware. These USB keys can securely store passwords, cryptographic keys, and digital certificates. The Nitrokey 3, for example, is PIN-protected and can be used for a variety of functions, from securing email communications with PGP to acting as a hardware wallet for cryptocurrencies. For a security expert, this tool can be integrated into a system to manage access to sensitive networks.
- Cypherock X1: This is a more advanced solution focused on the secure storage of private keys, particularly for crypto assets, but the principles apply to any high-value digital secret. It uses a unique multi-shard encryption system where the key is split across multiple NFC-enabled cards. This decentralized approach means there is no single point of failure, providing extreme security against theft or loss.
- Trusted Platform Module (TPM): A TPM is a dedicated microchip designed to secure hardware by integrating cryptographic keys into devices. It's a standard feature in most modern business-class laptops and many consumer PCs. A TPM can securely store network credentials, disk encryption keys, and digital certificates at the hardware level, making them extremely difficult to extract. In an enterprise setting, network access control systems can be configured to only allow connections from devices with a valid TPM, ensuring a very high level of corporate security.
Here’s a brief comparison of these hardware options:
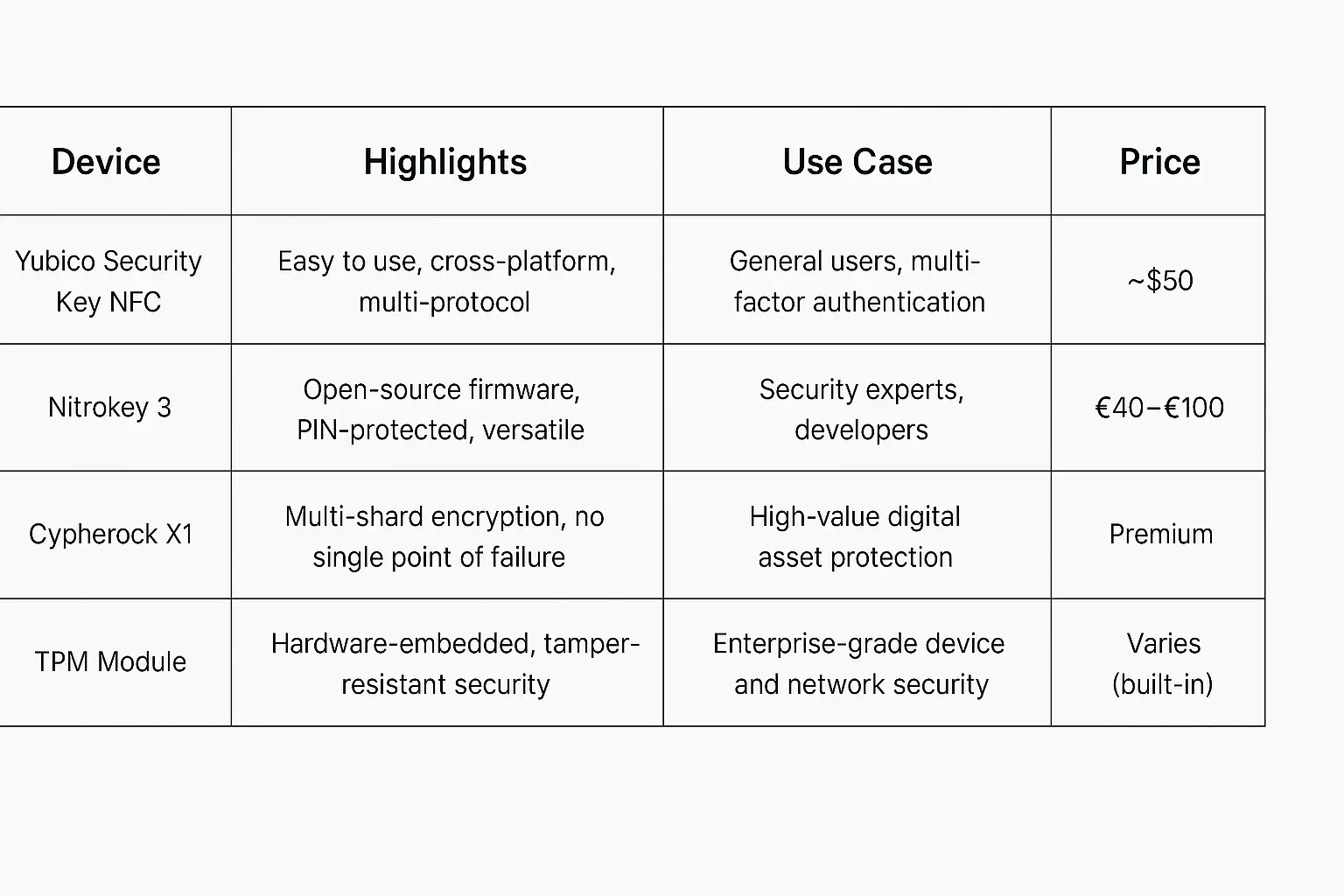
While these hardware solutions may be overkill for the average home user just looking to protect their Wi-Fi, they illustrate the depth of security available for protecting critical access credentials. For professionals, small businesses, or anyone handling sensitive data, investing in such hardware can provide peace of mind and a level of security that a simple Wi-Fi password alone cannot offer.
Troubleshooting Common Issues
Even with the correct network security key, you might occasionally run into connection problems. These issues can be frustrating, but they are often easy to resolve with a bit of systematic troubleshooting. Here are some of the most common problems related to the wireless security key and how to fix them.
- "Network Security Key Mismatch" Error: This is the most direct issue you'll face. It means the Wi-Fi password you entered does not match the one stored in the router.
- Double-Check the Password: The most common cause is a simple typo. Passwords are case-sensitive, so make sure "Caps Lock" is off. Carefully re-enter the key.
- Check for Correct Network: You might be accidentally trying to connect to a neighbor's network with a similar name. Verify that you have selected the correct SSID (network name).
- "Forget" the Network: Your device may have an old, outdated version of the key stored. Go to your device's Wi-Fi settings, select the network, and choose the "Forget" or "Remove" option. Then try connecting again, which will force you to re-enter the key.
- Device Won't Connect After Entering the Correct Key: Sometimes, the issue isn't the key itself but a temporary glitch in the communication between your device and the router.
- Restart Your Device and Router: This is the oldest trick in the IT book for a reason. Unplug your router from the power source, wait for 30 seconds, and plug it back in. While it's rebooting, restart the device you are trying to connect. This can clear up a host of temporary software and memory issues.
- Update Device Drivers and Router Firmware: Outdated software can cause compatibility problems. Ensure your computer's wireless network adapter drivers are up to date. Periodically, you should also log in to your router's admin panel and check for firmware updates. A secure router is an updated router.
- Forgetting the Key and Admin Password: If you've forgotten your custom Wi-Fi password and also changed and forgotten the router's admin password, you might feel locked out completely.
- Perform a Factory Reset: As a last resort, you can reset the router to its factory default settings. There is usually a small, recessed reset button on the back of the router. You'll need a paperclip or a similar object to press and hold it for about 10-15 seconds. This will erase all your custom settings, including the Wi-Fi name and password, and revert them to the default ones printed on the router's sticker. After the reset, you can log in with the default admin credentials and set up your network again. This is also a drastic but effective way to change Wi-Fi key settings when you're locked out.
By following these troubleshooting steps, you can resolve the vast majority of issues related to your network security key and get back online quickly and securely.
Frequently Asked Questions (FAQs)
Here are answers to some of the most common questions users have about their network security key.
- Can I see my network security key on my iPhone or Android device?
- Yes. On modern versions of Android (usually Android 10 and newer), you can go to your Wi-Fi settings, tap your connected network, and select "Share." This will show the Wi-Fi password below a QR code. On iPhones running iOS 16 or later, you can go to Settings > Wi-Fi, tap the "i" next to your network, and tap the password field to reveal it after authenticating with Face ID or your passcode.
- What’s better: WPA2 or WPA3?
- WPA3 encryption is definitively better and more secure than WPA2. It offers superior protection against password guessing (offline dictionary attacks) and provides enhanced security even on open, public networks. If your router and devices support WPA3 encryption, you should use it. WPA2 is still considered secure for most home use but is the older standard. The debate of WEP vs WPA2 is long settled, with WPA2 being vastly superior, and WPA3 now takes that security a step further.
- Is it safe to share my network security key?
- You should be very selective about who you share your main network security key with. Every person and device with the key has access to your local network. For visitors, it is much safer to enable a guest network. This provides them with internet access but keeps them isolated from your primary network and your personal devices.
- Can I change my Wi-Fi key from my phone?
- Yes, in most cases. You can access your router's administrative panel through a web browser on your phone, just as you would on a computer. Some router manufacturers also have dedicated mobile apps (like Netgear Nighthawk or Linksys Smart Wi-Fi) that make it very easy to manage settings, including the ability to change Wi-Fi key directly from your phone.
- How do I reset my router if I've forgotten the network security key and the admin password?
- If you've lost both the Wi-Fi and admin passwords, you'll need to perform a factory reset on the router. Find the physical reset button on the device (it's often small and recessed). Press and hold it with a paperclip for about 10-15 seconds until the router's lights flash, indicating it's rebooting. This will restore all settings, including the Wi-Fi password and admin login, to the defaults printed on the sticker on the router.
- How often should I really change my Wi-Fi password?
- For optimal security, it's a good practice to change Wi-Fi key every 3 to 6 months. This is a key part of learning how to protect Wi-Fi network resources. Regular changes minimize the risk from any previously shared or potentially compromised keys, ensuring your network remains secure over the long term.
Conclusion
The network security key, or your Wi-Fi password, is far more than just a random string of characters you enter to get online. It is the gatekeeper of your digital world, the primary defense mechanism that protects your personal information, your privacy, and the integrity of your home network. From preventing neighbors from slowing down your connection to blocking malicious attackers from stealing your data, a strong and well-managed wireless security key is an indispensable tool in your cybersecurity arsenal.
As we have explored, the strength of your key is intrinsically linked to the security protocol it uses. We strongly encourage you to move away from outdated standards like WEP and WPA, and even from the long-serving WPA2 if possible. Embracing the latest standard, WPA3 encryption, provides the most robust protection available against modern threats.
Take a moment to review your own home network security. Is your Wi-Fi password strong and unique? Is your router's firmware up to date? Are you using the highest level of security protocol available to you? By applying the principles outlined in this guide—from creating a formidable password and changing it regularly to utilizing features like guest networks—you can significantly enhance your digital defenses. In an era where our lives are increasingly lived online, taking proactive steps to secure router connections is not just a recommendation; it is an essential responsibility. Review your home Wi-Fi security now and ensure your digital front door is securely locked.
You've secured your local network, but how secure is your online presence? A professional, AI-driven website builds trust and expands your brand's reach. Wegic empowers you to create a stunning, high-performance website in minutes, simply by chatting with our AI. No code, no complications—just your vision brought to life.
Take the next step in strengthening your digital footprint.
Written by
Kimmy
Published on
Jul 28, 2025
Share article
Read more
Our latest blog
Webpages in a minute, powered by Wegic!
With Wegic, transform your needs into stunning, functional websites with advanced AI
Free trial with Wegic, build your site in a click!