Accesso
Construye Tu Sitio
What is the Dark Web? A Beginner's Guide to the Hidden Internet
Discover what is the dark web. This beginner's guide explains how it works, the deep web vs. dark web, risks, and legitimate uses.
The Internet is like a huge iceberg, far beyond the websites and applications we use every day.. The website you see in your daily search and browsing is just a small part floating on the water. Most of the content is hidden under the water. This is what we often call "Deep Web". In this deep web, there is a smaller and more hidden corner, called the "Dark Web". Many people have heard of the dark web but are confused. They may even be afraid of its true meaning and uses. This guide aims to uncover the mystery of the dark web, explaining "What is the Dark Web" in simple and clear language. This will help you understand this hidden cyberspace and how it works. The article will focus on its structure, access, potential risks, and often overlooked positive uses.

The three-layer structure of the Internet
To understand "what is the dark web", you first need to understand that the Internet is not a single level. It can be roughly divided into three layers.
- Surface Web
This is the Internet you use every day. It includes websites that can be easily found through search engines like Google and Bing. For example, news websites, blogs, social media platforms, and online stores. These websites are public and can be indexed by search engines.
- Deep Web
This is the largest part of the Internet, but it is inaccessible through regular search engines. It contains all content that requires login, authorization, or is behind a specific permission wall. For example, your private email inbox, online banking account page, internal company database, academic journals behind paywalls, membership websites, and medical record databases. The content of the dark web itself is not necessarily secret or illegal. It is just not indexed or requires permission to access. The deep web is very large, estimated to account for over 90% of the total Internet volume.
- Dark Web
The dark web is a very small subset of the deep web, requiring specific tools and configurations to access. It consists of a series of hidden websites. They use special technology, mostly "onion routing" (Tor), to mask their server location and visitor identity. All the dark web belongs to the deep web, but most of the content in the deep web is not the dark web. Understanding "what is the dark web" must include this inclusive but different relationship with the deep web. Dark web sites usually use domain names ending with ".onion". Ordinary browsers cannot open these sites. What is the dark web browser? It is the specific necessary tool to access this part of the network.
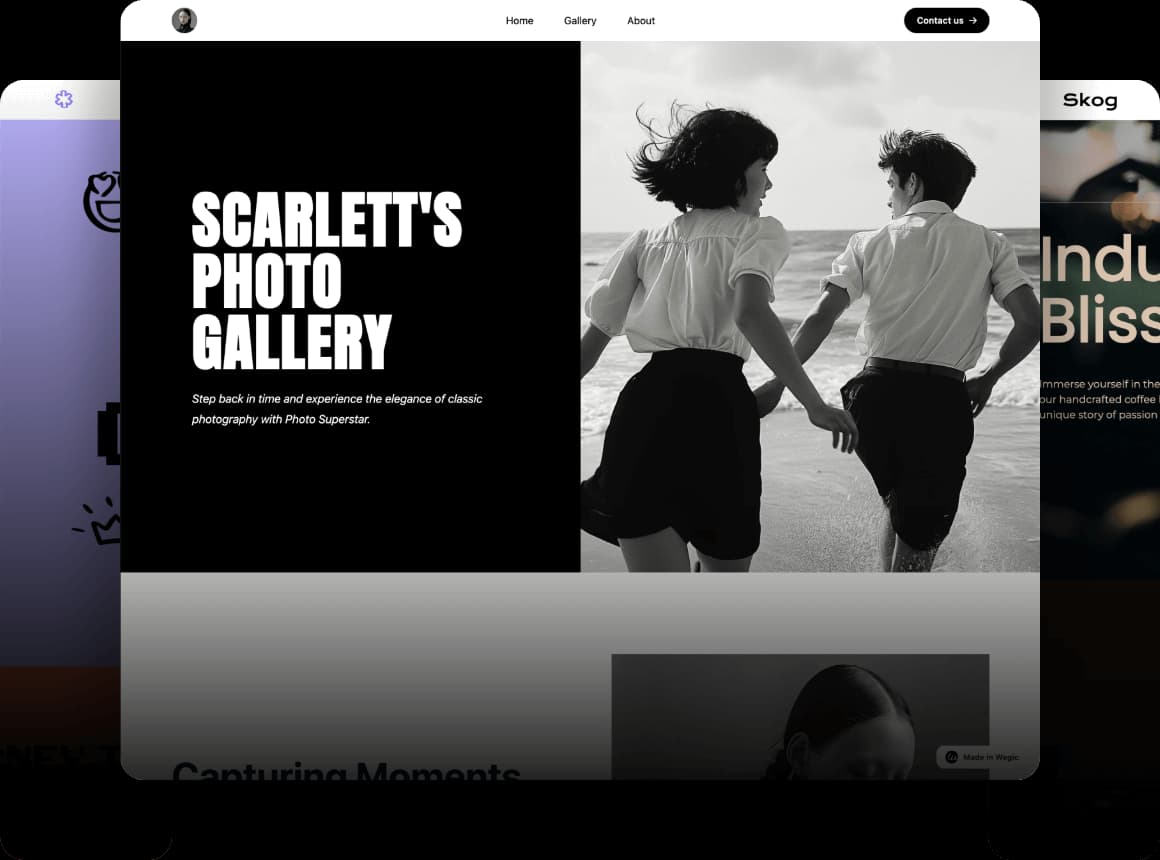
Click on the picture to explore the AI website builder👇
Features of the dark web
- Anonymity: The identity and location of users and website operators are highly hidden. This is its core feature. The key to understanding "what is the dark web website" is to recognize its design.
- Special tool access required: The dark web cannot be accessed using regular browsers such as Google Chrome, Firefox, or Safari. Specialized software must be used. The most famous one is the Tor browser (The Onion Router).
- Special website address: Dark web websites use the ".onion" domain name. Sometimes, they may use other similar technologies, such as the ".i2p" domain name of I2P. These addresses are like a string of random characters, which is difficult to remember. For example, http://example.onion.
- Content is not indexed publicly: Dark web websites will not appear in the results of mainstream search engines such as Google. To find these websites, users usually need to know the exact ".onion" address or rely on directories inside the dark web. These directories themselves may also be unreliable or outdated. This explains "what is the dark web in Google". Simply put, you can't find real dark web website content on Google.
How the dark web works
After understanding the definition, you will naturally want to ask, "What is the dark web and how does it work?" The core lies in anonymous technology.
- Tor (The Onion Router)
This is the most important technology to access the dark web. When users use the Tor browser, their network traffic is not sent directly from their computer to the target website.
- Encryption and relay
User requests are encrypted by Tor software, like onions. Then they are redirected through multiple, randomly selected computers called "nodes" or "relays" run by volunteers worldwide.
- Anonymous path
Every time the data passes through a node, the node is only responsible for decrypting a layer of "onion skin". That is to remove a layer of encryption. Each layer of encryption is visible to only one node. The guard node knows your IP address but doesn't understand the data content. The middle node only handles the decryption and transmission of the encryption layer. The exit node finally decrypts the data and sends it to the target website, thus knowing the request content. However, theoretically, it does not know the source of the request.
- Visit the ".onion" website
Eventually, the traffic reaches the target ".onion" website. The sites themselves also run on the Tor network. Since the ".onion" address contains routing information, access is completed directly within the Tor network. It doesn't need to pass through the exit node of the public Internet, further enhancing anonymity. This is the technical core of "What Is the Dark Web and How Is It Accessed?". It enables anonymous connections through multi-layer encryption and relay.
Click on the picture to build your website👇
Potential risks of accessing the dark web
While technology is neutral, visiting the dark web does have significant risks and must be taken seriously.
- Legal risks
The dark web contains illegal activities. Even if you just visit certain areas to browse, you may be accidentally exposed to illegal content or be in a legal gray area. Law enforcement agencies monitor the dark web, and your behavior may be recorded. Although the anonymous technology is complex, it is not unbreakable, especially when the user makes operational errors. Understanding "what is the dark web" must include an awareness of its legal boundaries.
- Malware and cyberthreats
The dark web is a hotbed of hackers, malware, and phishing activities. A website may contain malicious code designed to steal information, encrypted file ransomware, or control your device. The security risk is much higher than that of the surface web. Using an outdated browser or an insecure configuration can greatly increase the risk.
- Fraud
Due to high anonymity, scammers are rampant. The promised goods or services may not exist at all. Disappearing after payment is a common scam. There is no recourse mechanism.
- Psychological shock
What is on the dark web?You may be exposed to extreme, disturbing, or harmful content, even if you are not looking for it.
- Monitoring and Phishing
A malicious actor or law enforcement agency may set up false websites or services ("honeypots") to trap users or collect information. The Tor network itself may also have damaged nodes.
- Technical complexity leads to errors
Incorrectly configuring your browser, disabling security settings, or downloading unsafe files can all expose your true identity or infect your device.
If you ask, "What is the dark web and how do people access it?", it is strongly recommended that ordinary users do not access the dark web. You must take safe measures if you have to visit for legal reasons, such as research.
- Use only the official Tor browser and stay updated.
- Run on a virtual machine or a dedicated security device.
- Disable browser scripts via Tor's security settings.
- Never disclose any personal information or conduct financial transactions.
- Use a VPN. The effect is controversial, so you need to choose carefully.
- Make sure your purpose is to access only known and reliable resources, such as the ".onion" address of news organizations and libraries.

Legal uses of the dark web
Although dark webs are often associated with illegal activities, understanding "What Is the Dark Web" requires a comprehensive perspective. Its anonymity technology also protects many legitimate and even important purposes.
- Privacy protection: Citizen journalists, activists, and dissidents can organize, communicate, and share information anonymously through the dark web. For example, they can use Tor mail services and secure instant messaging platforms. It avoids censorship and surveillance. Whistleblowers can securely provide sensitive information to news organizations via Tor.
- Academic research and freedom of information: Scholars have access to databases restricted by certain countries. The library provides a channel for knowledge acquisition on the dark web. Open source projects and privacy technology developers use ".onion services" to distribute software, documents, and research reports that are not subject to censorship restrictions.
- Avoid censorship and content blockade: What is the dark web called? This term is also known as the darknet websites. Users can visit news websites, independent media, and social media platforms that are filtered and blocked by the government or ISPs locally. Normal search engines often refuse to index some niche websites and small community forums. However, they work properly under ".onion" addresses.
- Security testing and network research: Cybersecurity professionals can use the dark web to monitor potential threat intelligence. For instance, discussions of stolen credentials and previews of zero-day vulnerabilities. They can also study cyber attack method trends to develop better defense strategies and test system security in controlled environments.
- Digital rights and privacy advocacy: Privacy-focused individuals use dark web services like secure email hosting to reduce online tracking and data collection. Organizations such as the Electronic Frontier Foundation (EFF) have long supported the development of Tor technology and regarded it as a tool to defend basic privacy.
- Support sensitive dialogue: Professionals who need confidential communication or those seeking anonymous help can use the Tor Connection Service to communicate.
Understanding what is on the dark web cannot only focus on illegal sides. These positive uses prove the value of anonymous network technology, which protects basic human rights in a dangerous environment.
Use Wegic to build a safe website
Today, many privacy and security best practices are being integrated into modern website construction and maintenance. For example, consider using AI website-building tools like Wegic. Such platforms can significantly simplify the website creation process. More importantly, advanced tools may emphasize or build critical security measures. The safety demand is what we emphasize when you ask, "What is the dark web used for?"
Benefits of Wegic
- Zero technical threshold
Everyone can build a website. You don't need to learn HTML, CSS, JavaScript, or any programming knowledge. There is no need to understand server configuration or database management. You just need to describe your demand to the AI assistant, Kimmy. It's like you were talking to people. Wegic will understand your intentions and automatically generate the website.
- Amazing efficiency
Traditionally, it may take days or weeks to design, develop, and debug the website. The initial website can be built within 60 seconds by chatting with Kimmy. AI can instantly generate page layouts and copywriting. You just need to focus on providing ideas and feedback. AI is responsible for execution. This greatly shortens the cycle from idea to online. It is especially suitable for users who need to launch projects quickly.
- Intelligent design
Wegic is more than just executing commands. It can understand abstract style descriptions such as "fresh and natural" and transform them into concrete visual elements. This is equivalent to having an experienced designer and content strategist on call at any time.
Conclusion
What is the dark web? In this article, you will have a clear understanding of its definition. Although it's often related to illegal activities, we must admit that it also provides certain people with indispensable protection and free flow of information in a high-pressure review environment. Access to the dark web comes with real and significant risks and legal complexity. This requires extremely high security awareness and responsibility. On the other hand, technological innovations such as Wegic are reshaping the way websites are created. It can generate a website in one minute, breaking the technical threshold.
Whether you explore the dark web or use Wegic to build websites, the goal is to pursue a more autonomous and safer digital existence. The value of technology ultimately depends on how we use it. Adhering to safety, compliance, and responsibility is the core principle for navigating the digital world. Try Wegic now to build a perfect website!
Escrito por
Kimmy
Publicado el
Jul 16, 2025
Compartir artículo
Leer más
Nuestro último blog
¡Páginas web en un minuto, impulsadas por Wegic!
Con Wegic, transforma tus necesidades en sitios web impresionantes y funcionales con AI avanzada
Prueba gratuita con Wegic, ¡construye tu sitio en un clic!

